エンドツーエンドの暗号化、厳格なアクセス制御、厳密なセキュリティーポリシーでデータが保護されているため、安心してご利用いただけます。
広範なコンプライアンス認定や認証を活用して、複雑なグローバル規制環境下でも確実に事業運営できます。
Genesys の共有セキュリティーモデルなら、運用上の責任とコストを軽減できます。自社単独のセキュリティー対策よりも効果的です。
Genesys では、データとサービスの機密性、完全性、利用可能性を維持するために、多層式の防御戦略を採用しています。この手法では、セキュリティーメカニズムと制御の複数の層を実装します。制御が 1 つ失敗したり、脆弱性が悪用されたりした場合は、リスクを軽減する別の層が実装されます。
顧客データはすべて、転送時も保存時も暗号化されます。保存中のデータには AES 256 キー暗号化を、転送中のデータには TLS 1.2 以上の暗号化を使用する HTTPS を使用します。Genesys は、プラットフォームレベルの暗号化に加えて、通話記録のような機密データには、企業ごとに固有の暗号化キーを使用します。
プライバシー保護の重要度が全世界で高まるに伴い、規制の改正や地域基準を常に把握することは困難です。Genesys のプライバシー基準と設定可能ツールは、さまざまな業界や拠点においてグローバルなデータプライバシーのニーズを満たすために効果的です。
SAML 2.0 のサードパーティープロバイダーを使用したシングル・サイン・オンでアクセスを効率化します。多要素認証により、保護層を追加します。設定可能なアクセス権限では、最小権限の原則とロールベースの制御メカニズムを使用し、監査ログでは、ユーザーのアクティビティーを追跡します。
Amazon Web Services(AWS)内では、Genesys Cloud の本番サービスと顧客データが仮想プライベートクラウド(VPC)で論理的に分離され、セキュリティーが強化されます。VPC へのすべての接続は、パブリックインターネットを介して HTTPS と TLS 1.2 で保護されます。Genesys は、セキュリティーグループ、ロードバランサー、ルーティングの各設定に関する AWS のベストプラクティスに従います。
プラットフォーム API は、OAuth 2.0 仕様に従いセキュアに認証します。レート制限は、プラットフォームの安定性を確保し、悪意のあるサービス拒否攻撃から保護します。RESTful API には、セキュリティー上の固有の利点があり、データを暗号化して転送、ステートレス性、きめ細かなアクセス制御が可能です。
Genesys は、継続的な脆弱性スキャン、侵入テスト、導入前チェックを実施して、潜在的なリスクを回避します。ホストベースとネットワークベースの侵入検知システムが、疑わしいアクティビティーを監視します。特定されたセキュリティーリスクは迅速に修復されます。
AWS はデータセンターのセキュリティーを提供します。制御には、フェンシング、ウォール、セキュリティースタッフ、ビデオ監視、侵入検知システムなどの境界セキュリティーなどがあります。AWS データセンターに対する物理的アクセスはログに記録、監視、保持されるため、内部ユーザーによるセキュリティー脅威のリスクが軽減されます。
Genesys の情報セキュリティーとコンプライアンスチームは常時稼働しており、セキュリティー、監査、コンプライアンス、リスク管理を担当しています。また、すべての従業員に毎年セキュリティーとコンプライアンスのトレーニング修了を課しています。
Genesys Cloud™ プラットフォームは、世界中の数千社のお客様から信頼を得ており、公共部門、金融サービス、医療、公益事業などの規制の厳しい業界でデータを保護しています。Genesys の包括的なセキュリティー手法は、アプリケーション、インフラストラクチャー、プロセス、人材にまで及びます。顧客情報とビジネス情報の安全性、コンプライアンス、アクセス性が確保されるため、セキュリティーについて心配することなく、カスタマーエクスペリエンス向上に専念できます。
Genesys にとってセキュリティーは、お客様からの信頼に欠かせない要素です。セキュリティーに対する Genesys の包括的な手法は、プラットフォーム、プロセス、企業文化全体に組み込まれています。このアプローチは、情報に基づいた監視、効果的なリスク管理、一貫したセキュリティー慣行、厳格な監査、継続的なフィードバック、完全な透明性の原則に基づいています。
データの安全性とビジネスの保護を最優先にしたサービスであるため、お客様は安心してビジネスを運営できます。
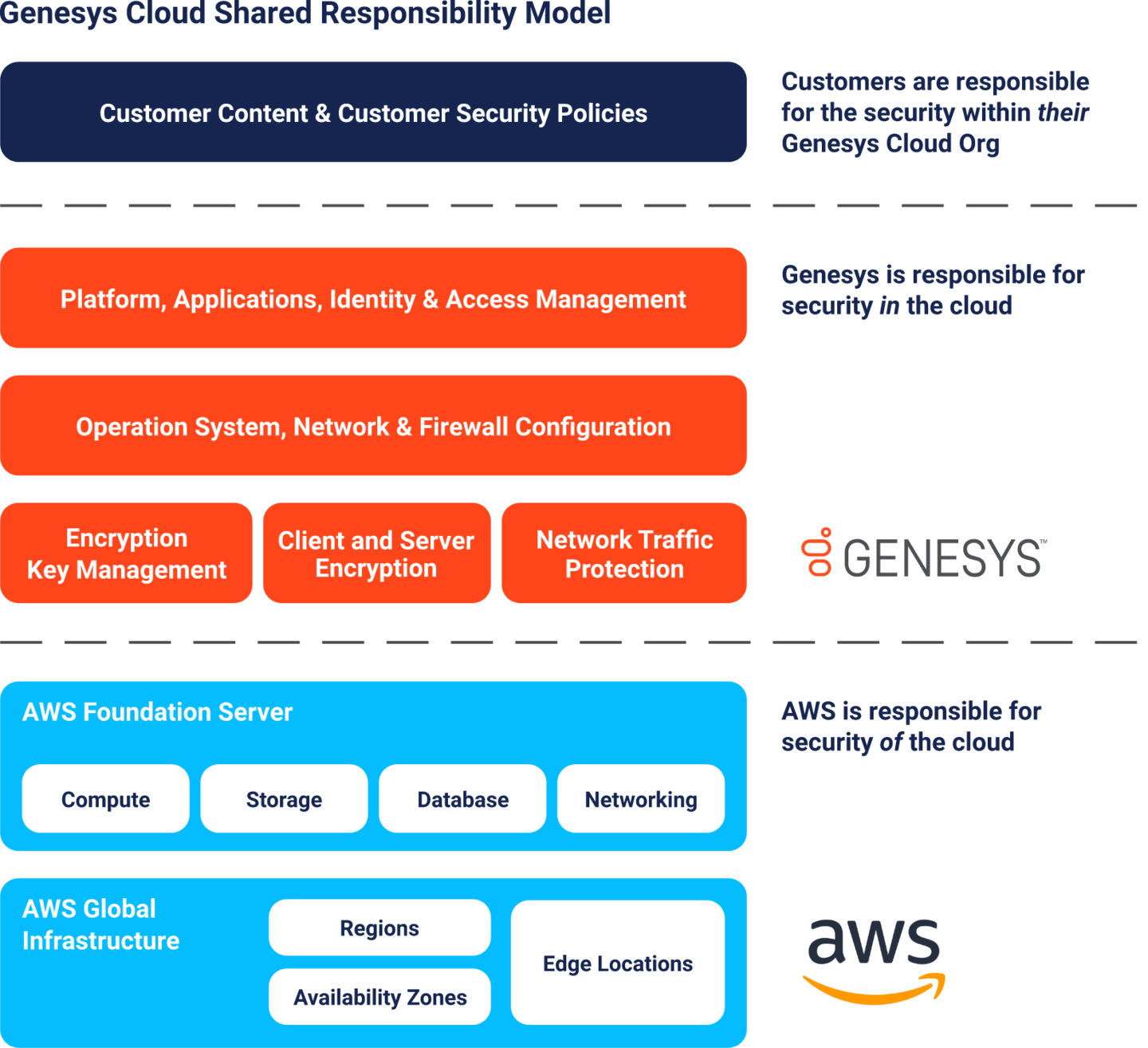
セキュリティーとコンプライアンスの管理に関する責任は、Genesys、クラウド・サービス・プロバイダー、ご利用企業の間で共有されます。AWS は、クラウド・コンピューティング・インフラストラクチャーのセキュリティーとコンプライアンスを運用し、管理します。Genesys は、クラウドでセキュリティーを管理します。ご利用企業は、Genesys Cloud を使用する企業内でセキュリティーの責任を負います。このように責任を分担すれば、運用上の負担が軽減され、多くの場合、企業単独で同程度のセキュリティーを維持するよりもコスト効率が向上します。
セキュリティープロトコルやセキュリティー対策を既存のソフトウェアに統合するのは優れた方法です。しかし、最初からクラウドネイティブのセキュリティーをソフトウェアに組み込む方がさらに優れています。Genesys では、DevOps の実施にセキュリティーが深い階層まで組み込まれています。Genesys の開発チームは、セキュリティーの原則を遵守しながら、Web アプリケーションのセキュリティーについて定期的にトレーニングを受けています。独立した製品セキュリティーチームは、新機能のリリース前に、セキュリティーコードの厳格なレビューとテストを実施しています。
現在のデジタルファーストの世界においてグローバルな規制コンプライアンスを実現することは高度な技術を要しますが、適切なパートナーを選べば問題を簡単に解決できます。Genesys は、業界のベストプラクティス、関連性の高い国際基準に加え、国内の法律にも対応しています。Genesys が幅広いコンプライアンスポートフォリオを維持していることは、お客様がどのような業界や地域で事業を展開していても、規制やコンプライアンスのニーズ以上の基準を満たすことができます。セキュアなプラットフォームを提供する Genesys の実力と取り組みを実証するものと言えるでしょう。
Genesys では、運用方法においてオープン性と透明性を重視しています。Genesys のトラストセンターは、Genesys のセキュリティーのベストプラクティスと幅広い業界や規制のコンプライアンスポートフォリオに関する詳細なインサイトを提供しています。お客様は、Genesys のライバシーポリシーや SLA など、Genesys Cloud の法的契約に簡単にアクセスできます。ステータスポータルでは、Genesys Cloud のリアルタイムと過去の運用パフォーマンスや、定期メンテナンスをご確認いただけます。Genesys の AI 倫理フレームワークと持続可能性への取り組みについても記載しています。地球の未来に積極的に貢献するという Genesys の取り組みをお分かりいただけるはずです。
セキュリティー対策を怠れば、評価の下落、消費者の信頼と信用の喪失、訴訟の可能性、収益の減少といった大きな損失を招きます。セキュリティー対策を怠る企業は、セキュリティー対策を行っている企業に顧客を奪われます。Genesys とのパートナーシップで、正しい知識とツールを活用して最新のグローバルなデータセキュリティーとコンプライアンスの基準を満たすことができます。まずはご連絡ください。Genesys がどのようにサポートできるかご説明いたします。
ご関心をお寄せいただき、誠にありがとうございます。
弊社担当より、折り返しスケジュール調整のご連絡をさせていただきます。
コンタクトセンターのコンプライアンスとは、地域、連邦、国際的な規制機関や立法機関により定められた一連の規制、基準、ガイドラインを遵守することを意味します。コンタクトセンターにとって、セキュリティーとコンプライアンスは不可欠です。優れたカスタマーサービスを提供し、個人データを保護して顧客の信頼を維持し、ビジネスの継続性を確保し、罰金や刑罰を回避するために欠かせない要素です。
国や業界、具体的なビジネスにより、コンタクトセンターが守るべきルールは異なります。法律やガイドラインは一般的に、データプライバシーとセキュリティーを確保しながら、不正行為やデータ漏洩を防止するためのものです。コールセンターのコンプライアンスに関する業界基準は世界各国で異なるものですが、共通した法令もいくつかあります。例えば、電話消費者保護法(TCPA)、一般データ保護規則(GDPR)、カード所有者データを保護するために策定されたクレジットカード業界のデータセキュリティー基準(PCI-DSS)などです。
Genesys は、複数の独立した第三者機関と定期的に関わりながら、Genesys が持つ認定に必要な監査を実施しています。さらに、Genesys の法務チームは、規則や規制を定期的に見直して、法規制に変更や追加があるかを確認しています。必要に応じて、コールセンターのセキュリティーポリシーと手順を最新の基準に合わせて更新します。
はい。Genesys Cloud プラットフォーム内で検出された潜在的なセキュリティーインシデントや、このプラットフォームに影響を及ぼすおそれのあるセキュリティーインシデントは、専門のセキュリティー・インシデント・レスポンス・チームに報告されます。このチームが有効化して遵守する Genesys インシデント・レスポンス・プランには、機密性、完全性、利用可能性への影響を最小限に抑えながら、分析、抑制、削除、復旧を行うための詳細なセキュリティーインシデント処理手順があります。