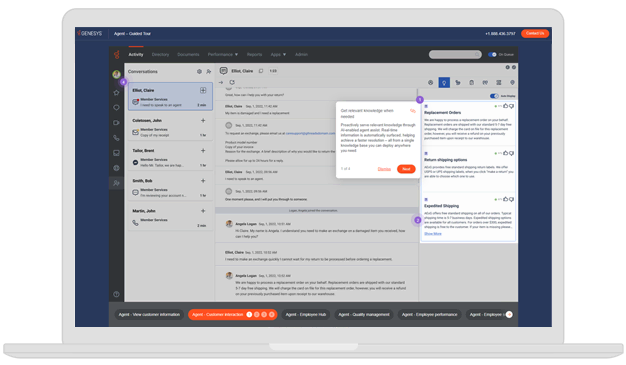
Start by identifying potential security risks, such as data breaches, unauthorized access and phishing. Next, review compliance requirements like GDPR, PCI-DSS and HIPAA to ensure the checklist meets regulatory standards.
Develop clear policies for user authentication, data encryption and real-time threat monitoring. Include regular password updates, secure workstation practices and access controls. Train employees on handling sensitive information and recognizing suspicious activity.
Finally, schedule routine audits and incident response drills to test the checklist’s effectiveness and update it as needed. A well-structured security checklist not only protects sensitive customer information but also builds trust and ensures operational continuity.