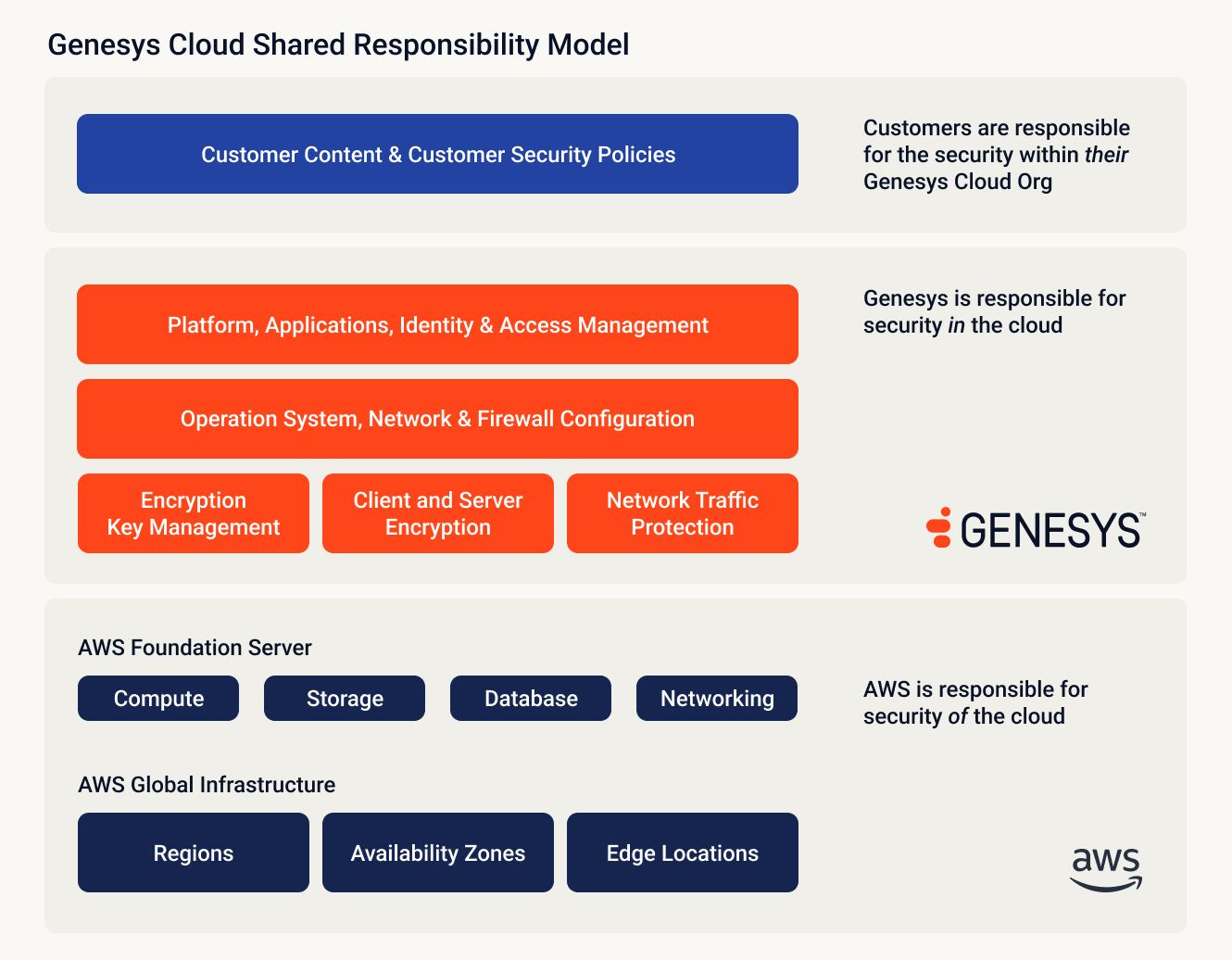
Genesys Cloud leverages the AWS secure infrastructure, strengthening it with industry standard network security controls designed to protect customer data. We follow AWS best practices for security groups, load balancers and routing configurations to ensure secure, efficient and reliable network services.
Each production environment is logically isolated within a virtual private cloud (VPC) for enhanced security. All connections between the Genesys Cloud VPC, browsers, mobile apps and other components are encrypted via HTTPS/TLS with AES-256 encryption, ensuring secure data transmission over the public internet. Additionally, authorized customer data connections between Genesys Cloud and third parties are conducted using secure methods and protocols (e.g., HTTPS, TLS, SFTP).




![Resource thumb [jpimedia]](https://www.genesys.com/media/resource-thumb_JPIMedia.webp)